TLS
Transport Layer Security (TLS), is a protocol to encrypt data sent over the internet. If you imagine packets being sent over the internet as stacks take a look at the below picture to capture where TLS fits into that.
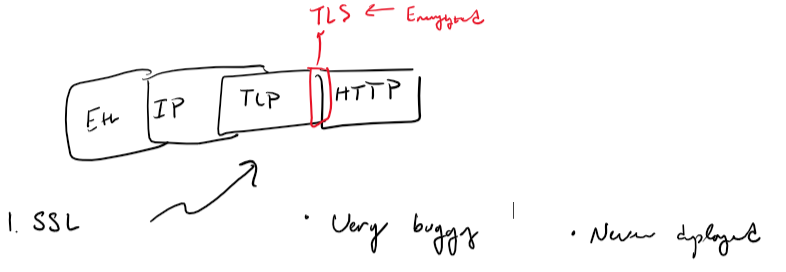
You can see the note I’ve made about SSL in the bottom left hand corner… As it turns out in the 1990’s researchers at Netscape used this architecture to develop SSL 1. Over the next few years, a few iterations of SSL later, an agreed upon protocol TLS 1.0 was made. The underlying technology being the same as discussed above.
TLS is a cryptographic protocol that sits on top of TCP, and can be used for any type of communication (not just HTTP). For communication to happen between two parties the following must be agreed upon.
- Cipher
- Secret Key
- Authentication
Let’s examine the handshake process.
TLS 1.2 Handshake
The first part of the handshake is the TCP Handshake. The client hello message will include the max TLS version supported by the client, a random number and a list of cipher suites. The server hello message will include a chosen TLS version, a random numberm, and a chosen cipher suite.
Once we know the parameters of the communication, the second part of this will be the server sending the client a certificate with a public key attached to it and a server key exchange message with a digital signature. Lastly, the server will send a server hello done message.
The client will reply with a client key exchange, a change cipher spec message, and a finish message containing an encrypted script of all the messages sent thus far. The server will then similiarily reply with change cipher spec and encrypted summary (finish messsage). This concludes the TLS handshake.
Links
https://www.youtube.com/watch?v=0TLDTodL7Lc
https://arxiv.org/pdf/1907.12762.pdf